The Time Machine — Weaponizing WaybackUrls for Recon, BugBounties , OSINT, Sensitive Endpoints and what not
You must have heard about time travel in movies, series and comics. Well here we are Nah i’m not joking you can travel back in time and can fetch the endpoints from web applications to do further exploitation, don’t believe me xD You will after Travelling from TheTimeMachine, PS Doesn’t work offline you need internet to Travel In Time xD.

I have created this tool for making my work easier when it comes to recon and fetching sensitive endpoints for sensitive data exposure and further exploitation using waybackurls aka The Time Machine and sorting for Sensitive endpoints, it has also option to look for sensitive endpoints for information disclosure, It has have more capabilities like looking for possible endpoints vulnerable to XSS, LFI, JIRA Based Vulnerability, Open Redirection.
I’m not too much into bug bounty but recently Managed HOF in NOKIA (Soon will be updated in Website or is already there :P), and found P1 with The Time Machine : https://bugcrowd.com/H4CK3R/crowdstream
It worked on multiple bug bounty program, reports are still under review :P
Lets get started.
Features
- Search for /api/ endpoint
- Search for JSON endpoint
- Fetch possible Conf(configuration) endpoint
- All Possible Sensitive instances in URL from TheTimeMachine (Searches from Fuzz List) or can also Add your own Custom List
- Fetches subdomains from waybackurl
- Search Custom keyword of your choice Eg. backup, .log etc.
- Attack Mode ( Searched for vulnerable possible endpoints for SQLi, LFI, XSS, Open Redirect, Wordpress, JIRA Based Vulnerability or via Custom File, PS More to be added soon )
- Fetch only Parameters from any file (Eg. Fetched from way back urls, extracted file from Attack mode or any URLs file, also how creative you are can be used with burp spider file :P)
- You can manually edit all the files that searched for XSS, LFI, Fuzz etc.
Installation
Steps for installation are pretty simple
Step 1.
Lets clone the repository from Github
$ git clone https://github.com/anmolksachan/TheTimeMachine
Step 2.
Install the required packages via requirements.txt or by simply running install.sh script.
$ ./install.sh
Tool in action — Recon, Possible Sensitive Endpoints & Sensitive Data Exposures
If the tool is not properly installed it will not run and will exit or if you’re not connected to internet it will not run.
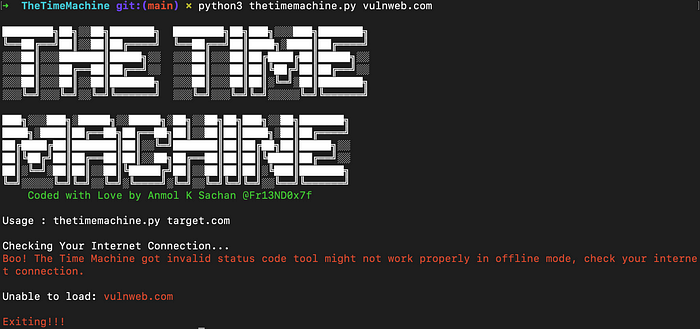
Lets run the tool on vulnweb.com
$ python3 thetimemachine.py vulnweb.com
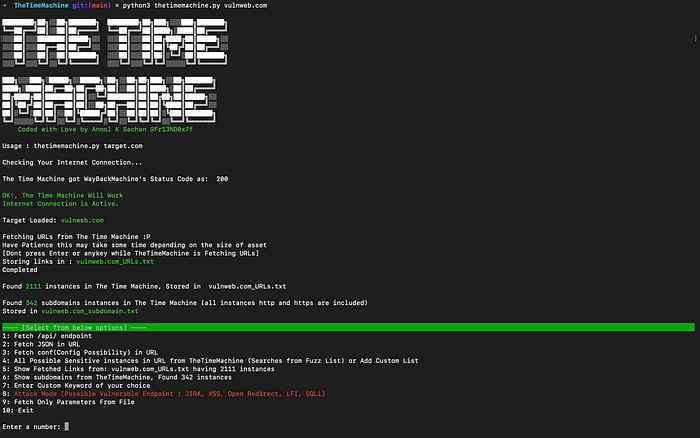
It will start passive recon and will create two files the first i.e target_URLs.txt having all the URLs from the Internet Archive and the second will fetch all the subdomains in target_subdomain.txt
You can use 5 and 6 to view target_URLs.txt & target_subdomain.txt
Lets start further, from selecting option 1, 2 and 3, they will start fetching for URLs having possible sensitive endpoints related to api, JSON, and config
Also my personal fav is 4, it gives us two options we can either use default fuzz build inside tool or can go for Custom list that you might have

You can also go with option 7 to search for your own juicy keyword for eg. phpmyadmin, jira etc.
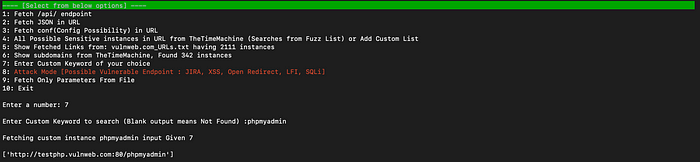
To fetch all parameters from the file you can go for option 9, for instance we will be using our target_URLs.txt to fetch all the parameters, also you can be creative here and can also give your burpsuite file that you can get from spidering the website, possibilities are endless.

All the parameters instances will be stored in targetfile_param.txt
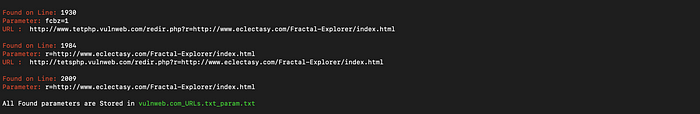
Tool in action — Possible Exploitable Endpoints (Attack Mode)
Option 8 is what i call “Attack Mode”, in here you can search for sensitive parameters vulnerable for XSS, Open Redirection, LFI, SQLi, Jira, Wordpress and what not

For instance on selecting option 1, its searched for endpoints that might be vulnerable to XSS

I recently got XSS in multiple VDPs including Harvard’s subdomain, vulnerability has been reported to the VDP of Harward
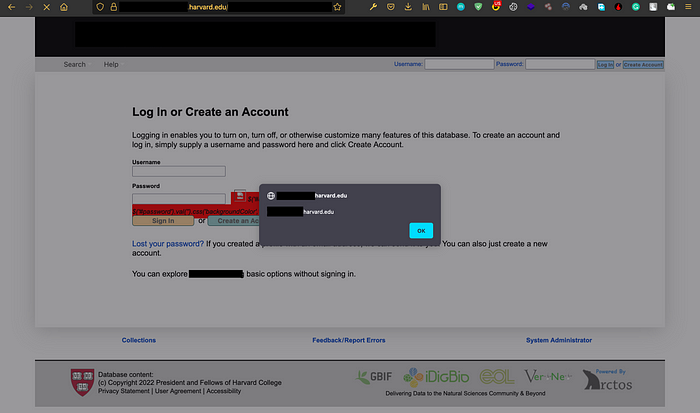
You can be creative with this tool and can also give custom Fuzz list for eg. https://github.com/danielmiessler/SecLists/tree/master/Discovery by using option 7
for eg. I found multiple vulnerability including Blind SSRF in Nokia, reported to VDP of NOKIA

Possibilities are endless, Its upto you how you travel with TheTimeMachine to understand the attack surface and seek for further exploitation.
